Investigators at the largest fuel pipeline in the US are working to recover from a devastating cyberattack.
The case of the Colonial Pipeline is one of the most significant attacks on critical infrastructure in the US. The criminal platform behind the attack, ‘DarkSide’, is a known entity that has hacked other large corporations in the past.
But when a ransomware cyber attack strikes, what happens behind the scenes remains largely hidden from the public eye. One such element are the ransom negotiations with the attackers. Brian Krebs, a well-respected blogger in the cyber security domain has released inside chat protocols that describe these negotiations. The chats come from a previous negotiation with DarkSide, the same hacking group that paralysed the fuel pipelines in the US.
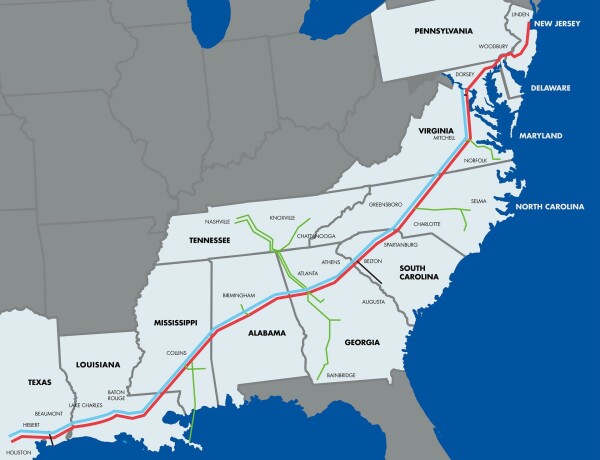
Colonial Pipeline has shut down 5,500 miles of fuel pipe in response to a ransomware incident.
Image credit: colpipe.com
Summary:
-
DarkSide is a ransomware-as-a-service platform, that allows vetted criminals to use their ransomware services to attack companies, and to negotiate with victims. But, DarkSide states that it doesn’t allow attacks on some industries, such as healthcare or education.
-
After the ransomware struck, the first chat protocols are about establishing trust between the parties: “How do I know that you can decrypt our data?” – “We can decrypt one sample file for you.”
-
The initial ransom demand was $30 million, and the first counteroffer of the victim was $2.25 million.
-
After back and forth, and some countdowns, DarkSide finally accepted a payment of $11 million – almost one third of the original price.
-
Part of the negotiations include certain things other than the price itself, such as an assurance that the criminal gang won’t attack again, and agreements that DarkSide will not sell or publish any data.
-
Overall, the chats give an interesting insight into negotiations that remain largely hidden from the public eye.
Why does this matter for businesses?
-
Ransomware is a growing threat to businesses. The negotiations are a key element of the recovery of data, and even the prevention of public data loss.
-
The article shares screenshots from these negotiations, which may give businesses a good sense of what to expect in the case of a ransomware cyber attack.