This comprehensive report from Carnegie Mellon University (2022) analyses 3,000 cases of insider threat to provide 22 evidence-based best practices for organisations.
According to the survey, termination and resignation are the two most common stressors leading to an insider incident. Email, removable media, and paper are the most common data exfiltration methods. The finance and insurance industry, as well as public administration, are most prone to insider attacks, whereas real estate, construction, and agriculture are the least prone.
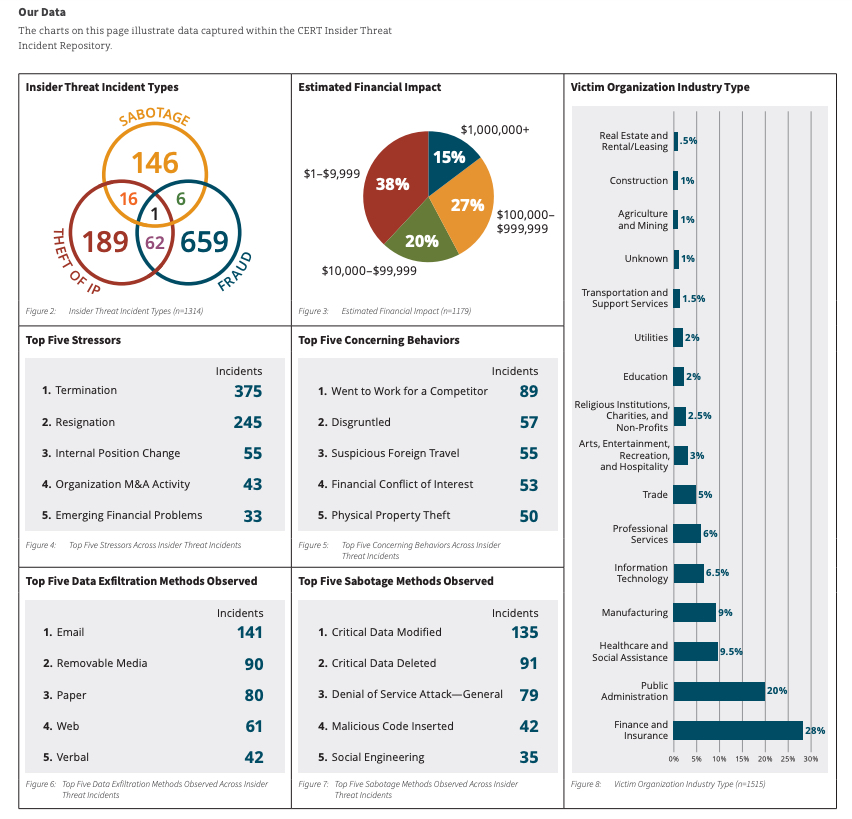
Source: Common Sense Guide to Mitigating Insider Threats, 2022, Carnegie Mellon University
The report offers 22 best practices in dealing with insider threat and risk. They are:
- Know and Protect Your Critical Assets
- Develop a Formalised Insider Risk Management Program
- Clearly Document and Consistently Enforce Administrative Controls
- Beginning With the Hiring Process, Monitor and Respond to Suspicious or Disruptive Behaviour
- Anticipate and Manage Negative Issues in the Work Environment
- Consider Threats From Insiders and Trusted External Entities in Enterprise-Wide Risk Assessments
- Be Especially Vigilant Regarding Social Media
- Structure Management and Tasks to Minimise Insider Stress and Mistakes
- Incorporate Insider Threat Awareness Into Periodic Security Training for All Workforce Members
- Implement Strict Password and Account Management Policies and Practices
- Institute Stringent Access Controls and Monitoring Policies on Privileged Users
- Deploy Solutions for Monitoring Workforce Member Actions and Correlating Information from Multiple Data Sources
- Monitor and Control Remote Access from All Endpoints, Including Mobile Devices
- Establish a Baseline of Normal Behavior for Both Networks and Workforce Members
- Enforce Separation of Duties and Least Privilege
- Define Explicit Security Agreements for Cloud Services, Especially Access Restrictions and Monitoring Capabilities
- Institutionalize System Change Controls
- Implement Secure Backup and Recovery Processes
- Mitigate Unauthorised Data Exfiltration
- Develop a Comprehensive Workforce Member Termination Procedure
- Adopt Positive Incentives to Align the Workforce and the Organization
- Learn From Past Insider Threat Incidents
The full report describes how companies can implement each of the best practices.