This Google report provides a year-long review of zero-day exploits in the wild in 2023. What are the trends, gaps, lessons learned and successes of 2023?
Stats on zero-day exploitation in 2023:
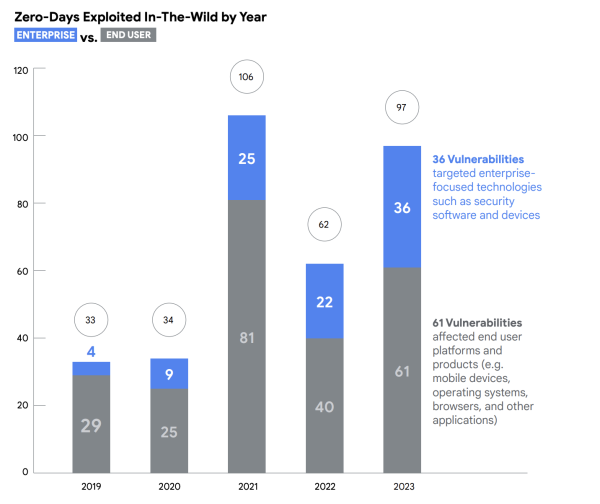
- Google observed 97 zero-day vulnerabilities exploited in 2023 - a 50% increase over 2022, but less than the 106 recorded in 2021.
- Google categorises the exploits into two categories: platforms and products like browsers and mobile devices that people use in their everyday lives, of which there were 61 vulnerabilities, and enterprise-focused technologies, of which there were 36.
Source: A review of zero-day in-the-wild exploits in 2023 (Google)
- Enterprise targeting is on the rise - seeing a 64% increase between 2022 and 2023 - due to the growing exploitation of security software and appliances.
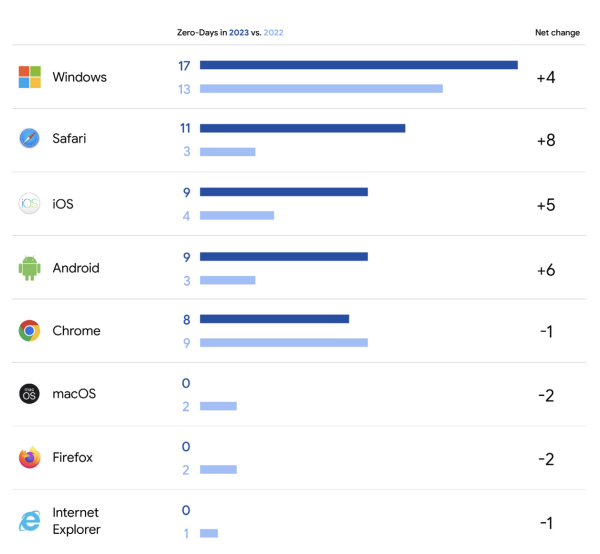
- In end-user products, Windows, Safari and iOS saw the biggest increase in zero-days. The macOS operating system suffered from no zero-day vulnerabilities in 2023.
Source: A review of zero-day in-the-wild exploits in 2023 (Google)
- Commercial surveillance vendors, which develop and sell spyware to government customers, were responsible for 64% of zero-day exploits of mobile devices and browsers. Espionage accounted for 41.4% of the zero-day vulnerabilities.
- The number of exploits helmed by financially motivated actors decreased between 2022 and 2023, standing at only 17%, a significant drop from a third of exploits in 2021.
Insights into targets:
- Investments from companies on the end-user side, like Google, Microsoft, and Apple have vastly diminished the number of zero-days that malicious actors can exploit. Developing tools like Apple’s Lockdown setting, which switches a user’s device into high-security mode, has paid off.
- But attacks on enterprise software—particularly security software—are only increasing. This software is of particular interest to hackers because it has a high level of permissions and access, clearing a pathway into the organisation.
- Zero-day vulnerabilities in third party components also pose a major challenge for cybersecurity defenders. Their prevalence among a number of different products makes them more valuable to hackers.