With 50% of cybersecurity breaches caused by insiders, many businesses are enacting blanket policies that monitor all of their employees to help tackle this risk. But according to this article, these typical approaches - which attempt to identify abnormal behaviour from each user in hopes of stopping a breach in its tracks - aren’t adequate in countering the threat.
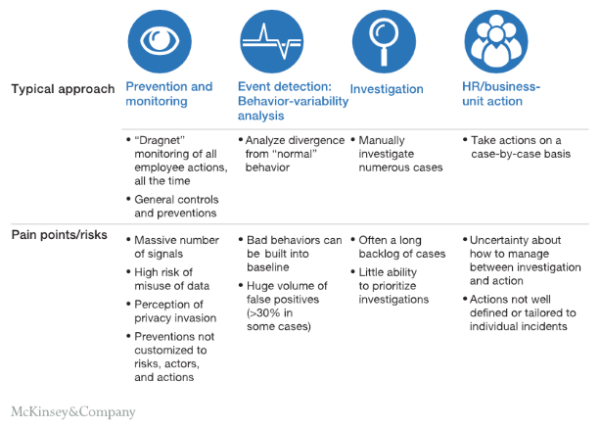
They risk violating users’ privacy and mishandling their data, often identify the risk too late, generate many false positives, and don’t provide a solution for catching serial bad actors. Stopping insider threats should begin with understanding malicious actors and what motivates them.
Instead, the article published by McKinsey outlines three approaches that seem to be more effective:
1. Microsegmentation
Microsegmentation involves identifying the groups of employees who are most capable of insider threats and concentrating preventative efforts on them - in other words, the “hotspots”. For instance, businesses should seek to understand which employees have access to the most sensitive information, and conduct a focused intervention by creating tailored strategies to monitor and mitigate insider events. This could be done by educating them on cybersecurity best practices to reduce the risk of negligence. They should also instigate programmes to boost employee satisfaction, reducing the risk of disgruntled employees deliberately committing breaches. By aiming scrutiny at segmented groups rather than individuals, microsegmentation also improves privacy.
2. Culture change
Many programmes focus on catching and responding to negative behaviours, but they should also address the cultural issues that drive negligence and malicious behaviour in the first place. Cultural issues and wider workplace attitudes also impact the likelihood of insider threats. Firstly, to combat breaches that occur due to negligence, cybersecurity training should aim to help shift employees' attitudes and beliefs about the importance of cybersecurity, while leadership influence can go a long way towards securing buy-in.
This strategy also involves tackling the motivations of malicious actors, which may include dissatisfaction with management, personal financial issues, and lack of promotion. Businesses need to proactively identify and address these issues by conducting regular surveys and taking steps to address any problems they reveal, such as putting leaders on management training or providing financial advice services.
3. Prediction
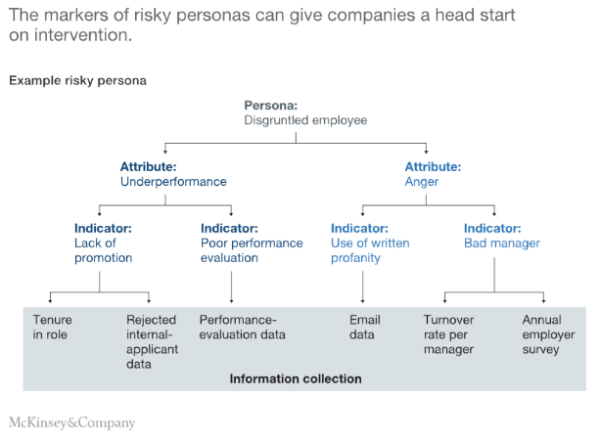
Some organisations are implementing predictive insider-persona analytics, which involves identifying the characteristics of the individuals or groups most at risk of attacking an organisation. These organisations look at key personas that are high risk instead of waiting for anomalies in user behaviour. For instance, one such persona is known as a disgruntled employee - who can be identified by underperformance and anger, with this information collated through performance evaluation data, email data, and employee surveys.