Hybrid warfare is nothing new: it’s the use of nonmilitary tactics alongside conventional kinetic warfare to achieve foreign policy goals. Most militaries around the world have added cyber as the fourth domain of warfare, alongside land, sea, and air.
Russia has long been experimenting with hybrid warfare techniques but has ramped up the use of digital technology to surveil, disrupt, corrupt, or destroy digital infrastructure since the invasion of Ukraine.
This article analyses the evolution of cyber operations in armed conflicts. It first looks at the different threat actors operating in the cyber domain:
- States have military and intelligence agencies that conduct cyber operations as part of their foreign policy strategy
- Cybercriminals are nonstate actors who are primarily motivated by profit
- Hacktivists are also nonstate actors but are motivated by activism, with a political motive
- Terrorist groups are nonstate actors who are ideologically motivated and often seek to sow discord
- Cyber mercenaries are for-hire, private cyber operatives who state or nonstate actors contract for specific operations
Although many people tend to associate cyber operations with Russia, they are not solely a Russian domain.
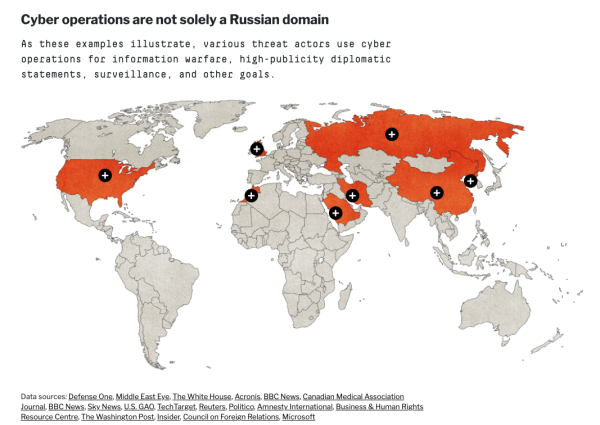
Source: digitalfrontlines.io
However, Russia has tested their cyber capabilities over the past decade in Ukraine and launched attacks on infrastructure shortly before invading Ukraine. The cyberattack on the Viasat satellite network just hours before the Russian invasion of Ukraine had a cascading effect across the region. For a short period, satellite military communications in Ukraine were disrupted, but the attack spread, and German energy company Enercon reported losing remote control of 5,800 wind turbines across central Europe.
Russia’s groundwork for hybrid warfare dates back to 2013. Leading up to the invasion, cyberattacks have ramped up.
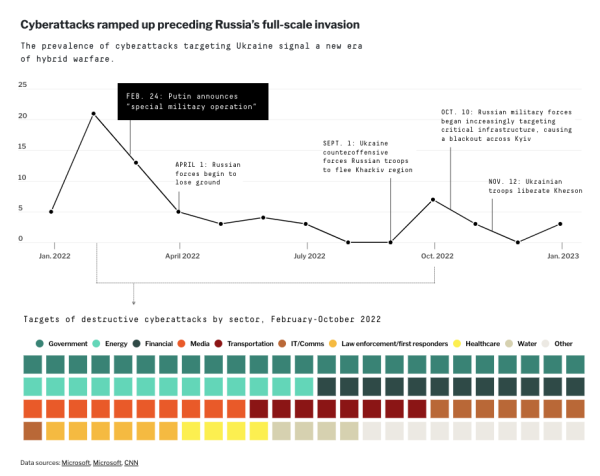
Source: digitalfrontlines.io
The problem of attributing cyberattacks can undermine responses. Attacks can go unnoticed for months, complicating timely responses. In addition, governments might decide to use mercenaries or hacker groups to conduct attacks, thereby relying on plausible deniability of their involvement.
Why does this matter for businesses?
- Businesses are part of a domain that is contested and used by nation-states to carry out their strategic goals. That means they can be targeted directly or indirectly get harmed by cyberattacks originating from nation-state attackers.
- What helped Ukraine was a truly global, collaborative approach between private companies such as Microsoft, governments, and intelligence agencies. That approach is the reason why Ukraine is still online.