This report explores how many organisations were hit by ransomware hacks over the last year, why attacks are getting worse, and what recovery looks like.
The good news is that organisations seem to be getting a grip on ransomware.
Key ransomware stats:
- 59% of organisations were affected by ransomware in the last year, a minor fall from 66% in 2022 and 2021. In general, the higher the revenue, the more likely a company was to suffer an attack - but even among the smallest organisations, with a revenue of under $10m, almost half were hit.
- Central and federal governments had the highest rate of ransomware incidents across all industries (68%), potentially due to an increase in politically motivated attacks. In terms of geography, France had the highest rate at 74%, followed by South Africa at 69% and Italy at 68%.
- Only 4% of the organisations impacted by ransomware reported that 91% or more of their devices were impacted.
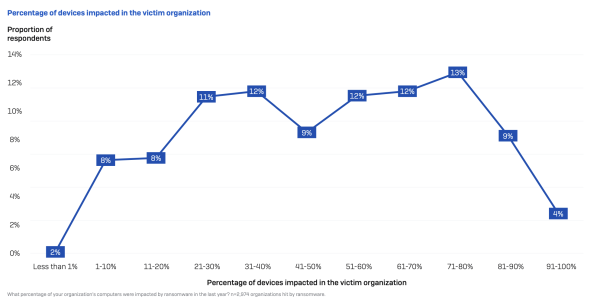
Source: Sophos, State of Ransomware 2024
The root cause of ransomware attacks:
- Exploited vulnerability was the highest-ranked cause of an attack (32%). These attacks tend to have more damaging consequences than those that can be traced back to compromised credentials (29%) - affected organisations are more likely to pay the ransom and have 4X higher recovery costs.
- 23% of attacks stemmed from a malicious email, and 11% from phishing, pointing to the need to equip employees to counter email-based threats.
Intensifying damage:
- Hackers often seize a company’s backup systems — attempting to do so in 94% of cases, where 57% are successful — cutting off the organisation’s chances of restoring its data. In cases where backups were impacted, ransom sums doubled, as did the likelihood the victim would pay up.
- 32% of attacks involved data theft, often leading to hackers selling it on the dark web. While recorded rates of data theft vary across industries, this could be attributed to the uneven availability of tools that can identify when this has occurred.
Data recovery:
- Where data was encrypted, 98% of organisations managed to recover it, whether from backups (68%), paying the ransom (56%), or other means, like working with law enforcement (26%). Almost half used more than one method to recoup their data.
Paying the ransom:
- The cost of a ransomware attack is escalating—the median payment is now $2m, a 5X increase from last year, while the mean payment is $3.9m, a 2.6X increase.
- Among the largest organisations by revenue, 61% paid the ransom, while only a quarter of the smallest organisations paid, likely because they lacked the funds to do so.
- A quarter of respondents met the hackers’ demands exactly, while 44% paid less and 31% paid more. Of all sectors, higher education and healthcare were the most likely to pay more - potentially due to an eagerness to recover data as quickly as possible in order to deliver vital public services.
Recovery:
- Organisations’ recovery time is slowing down - for over a third of victims, it took over a month, possibly because attacks are growing increasingly complex. Unsurprisingly, this prolonged recovery time was exacerbated if the organisations’ backups were compromised.