When the CL0P ransomware gang from Russia (also known as TA505) exploited a zero-day SQL injection vulnerability to hack Progress Software's MOVEit Transfer app, it soon became evident that a significant number of organisations and individuals would be impacted. Attackers exploited a vulnerability to escalate their privileges, allowing them to gain access to thousands of organisations’ and millions of individual users’ MOVEit Transfer databases and to exfiltrate and/or alter files.
Supply chain attacks are not uncommon, but this one was particularly wide-reaching, with data being stolen from governments, businesses and educational organisations worldwide. As the gravity of the situation unfolded, Progress Software moved swiftly to address the breach, patching the exploited vulnerability and identifying other critical MOVEit Transfer vulnerabilities.
Recent research shows that over 60% of U.S. businesses have faced software supply chain threats (similar to the MOVEit Transfer attack) in the past year as attackers increasingly are targeting supply chains in their tactics and operations. Compromises originating in attacks on business partners, such as supply chain breaches, are particularly severe, costing 11.8% more and taking 12.8% longer to identify and contain than direct attacks, according to IBM’s Cost of a Data Breach Report 2023.
The challenges of cyber risks in the supply chain
Organisations have to manage an overwhelming number of suppliers. For instance, imagine a retail giant that sources products globally from diverse suppliers, ranging from manufacturers and distributors to local vendors. The sheer scale of this supplier network amplifies the difficulty in maintaining robust cybersecurity across the entire chain. Typically, large enterprises have 5,000 to 10,000 or more suppliers, while medium enterprises might have 1,000 to 3,000. When it comes to managing the cyber risk associated with those suppliers, companies often encounter the following three challenges.
1. The rising tide of compliance pressure
Regulatory pressures are intensifying, and compliance requirements are evolving, placing additional burdens on organisations to ensure the security and integrity of their supply chain. The U.S. president’s Executive Order from May 2021 is just one instance of the growing scrutiny.
2. Inadequacy of traditional third-party management
Traditional approaches to third-party supply chain management, often based on contract size or hierarchical tiering, are proven to be inadequate. Seemingly “insignificant” suppliers can become potential stepping stones for cyber threats. This challenges the conventional method of tiering suppliers based solely on their contractual value, emphasising the need for a more nuanced approach that considers the cybersecurity posture of each vendor, regardless of their size.
3. Questionnaire fatigue and inefficient processes
Traditional questionnaire-based cyber assessments of third parties pose challenges, as they are merely point-in-time evaluations. This approach puts immense pressure on organisations for timely risk mitigation. Organisations may also struggle with evaluating risk if vendors delay their responses and actions in an ongoing risk remediation plan.
These challenges are compounded by broader cybersecurity issues within the enterprise, such as lack of visibility across the supply chain, budget constraints and/or staff shortages.
Three objectives to help tackle third-party cyber risks
To successfully address cybersecurity risks throughout the supply chain, businesses should start with strategic and tactical objectives across three dimensions: enterprise alignment, programme governance and process transformation. Below is an illustrative table that outlines these objectives.
|
Strategic Objectives |
Tactical Objectives |
|
|---|---|---|
| Enterprise Alignment | Enable critical cyber-risk decisions by aligning with enterprise risk management and closer collaboration with procurement, IT and cyber risk management teams. | Establish continuous risk monitoring for critical and high-risk vendors to analyze external vulnerabilities and risks in real-time through technology integration and service management processes. |
| Programme Governance | Establish a steering committee to oversee risk management, security incident and risk acceptance reviews and vendor onboarding. | Enhance security risk assessments for new and existing vendors by leveraging GRC tools and adaptive questionnaires. |
| Process Transformation | Establish a framework, a policy and an operating model to uplift cyber risk management capabilities, including a risk-tiering model and an efficient risk remediation engine. | Effective risk reduction through ongoing tracking and monitoring of remediation plans and real-time management reporting. |
Implementing a roadmap to achieve the objectives
Once your objectives are clear, a roadmap that includes a combination of technology capabilities, leading industry practices and advisory experience should be defined. The three steps in the roadmap below highlight the need for solving tactical problems as an initial step, resulting in greater visibility of present risks. Then, organisations should prioritise building capabilities that will transform the risk management and governance process. The final stage is risk remediation.
Adaptable and modular approach across three phases
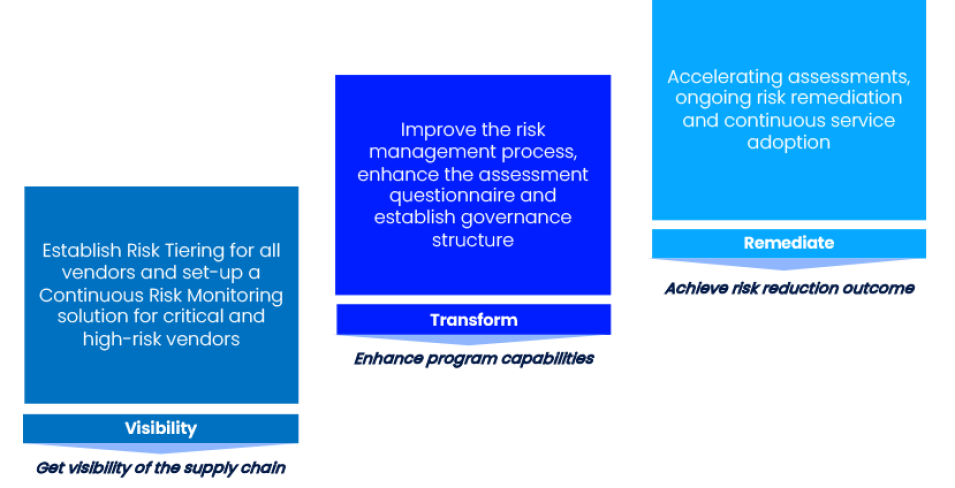
© ISTARI Global Limited 2023. All rights reserved.
The value of boosting supply chain cyber risk management
Adopting a proactive approach to supply chain risk management has at least four advantages for businesses, such as:
- Comprehensive visibility of supply chain risks allows for prioritisation based on the criticality of vendors, providing a better understanding of potential threats and enabling informed decision-making.
- Efficient resource allocation through a risk-based approach to vendor tiering. This strategy establishes trigger logic for risk assessments, allowing businesses to focus on vendors with higher risk profiles and directing resources where they’re most needed.
- More resilient and adaptable operations are achieved through a blend of integrating supply chain risk with broader enterprise risk management. This alignment strengthens cyber risk management practices and contributes to the creation of a resilient and adaptable supply chain through better collaboration.
- Better risk remediation through an agile approach to the organisation’s risk remediation engine to expedite remediation plans. By being more dynamic, it’s possible to minimise the window of exposure, enhancing the organisation's ability to mitigate potential threats.







